ShellBuster
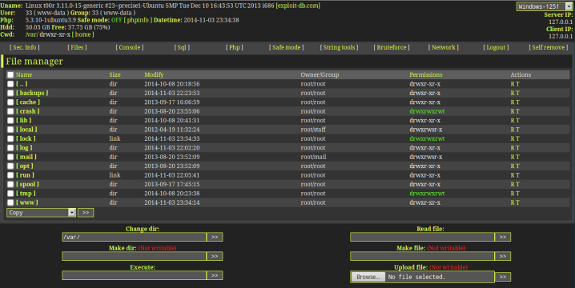
Computers can get computer malware. Websites can get web shells. If your server has a web shell, odds are you've been compromised. Scanning is important, even if it is a reactive security approach, as opposed to proactive.
When I was teaching myself about web security, one particular area that piqued my interested was file inclusion and file upload vulnerabilities, as well as web shells. Web shells are often able to be used with a website if it has RFI/LFI or upload vulnerabilities. These are issues that mainly affect PHP.
ShellBuster is a project I am working on that will enumerate directories and files on a web server and then parse the files for certain strings that are commonly found on web shells. Some indicators of compromise are generic, but others are specific to certain shells.
Of course, this approach isn't perfect, as a lot of malware these days is polymorphic. It wouldn't be that hard to change up a web shell enough that traditional signature and detection methods won't pick it up. The future of security scanning is heuristic analysis and machine learning, such as with TensorFlow. But that's a little too advanced for me right now.
Scanning is not an all-ecompassing security solution, but many people are too quick to dismiss it. It is simply another tool to add to your security repertoire. Additionally, web shells aren't the only security issue web developers face today. OWASP, the Open Web Application Security Project, details a lot of other security issues too. But this project doesn't aim to solve every single security issue ever. It focuses in on a very specific problem rather than trying to do everything.
Scope creep is a serious problem in software development. It's important to know what your program will and will not do. This program only deals with web shells, and nothing else.
ShellBuster is on GitHub here and the BadExif repo is here
